Small Businesses Failing at Cybersecurity: Why They Are So Attractive to Hackers
Small businesses are increasingly becoming targets of cyber-attacks, and the consequences can be devastating. While larger organizations often have robust cybersecurity measures in place, small businesses may lack the necessary resources and expertise to effectively protect against cyber threats.
Read MoreMicrosoft 365 Prices Increasing
Did You Know That Microsoft Is Increasing Their Prices on April 1st? If you’re using Microsoft products, you might want to brace yourself—Microsoft is increasing their prices starting April 1st, 2025. Whether you’re a business owner, IT administrator, or an individual user, this change could impact your budget. Let’s break down what’s happening, why Microsoft […]
Read MoreWhat Equity, Respect, and Voice Mean to Me
Cyproteck Technologies and CGD LLC Company history It all started in Corporate America… What Equity, Respect, and Voice Mean to Me This topic is deeply personal to me, and I took the time to truly reflect on what equity, respect, and voice mean—not just as concepts, but as core principles that guide me in […]
Read MoreWhat is Endpoint Detection & Response?
The main function of EDR is to provide continuous monitoring of endpoint devices to detect and respond to security incidents.
Read MoreWhat are Compliance Reports?
Compliance reports provide a detailed analysis of an organization’s compliance with industry regulations and standards, such as HIPAA, PCI DSS, and GDPR.
Read MoreAutomated Incident Response & Forensics
Automated incident response and forensics solutions use artificial intelligence and machine learning to identify, contain, and mitigate security incidents.
Read MoreIncident Response: A Crucial Component of Cybersecurity
Incident response (IR) is a process that responds to and manage the aftermath of a security incident.
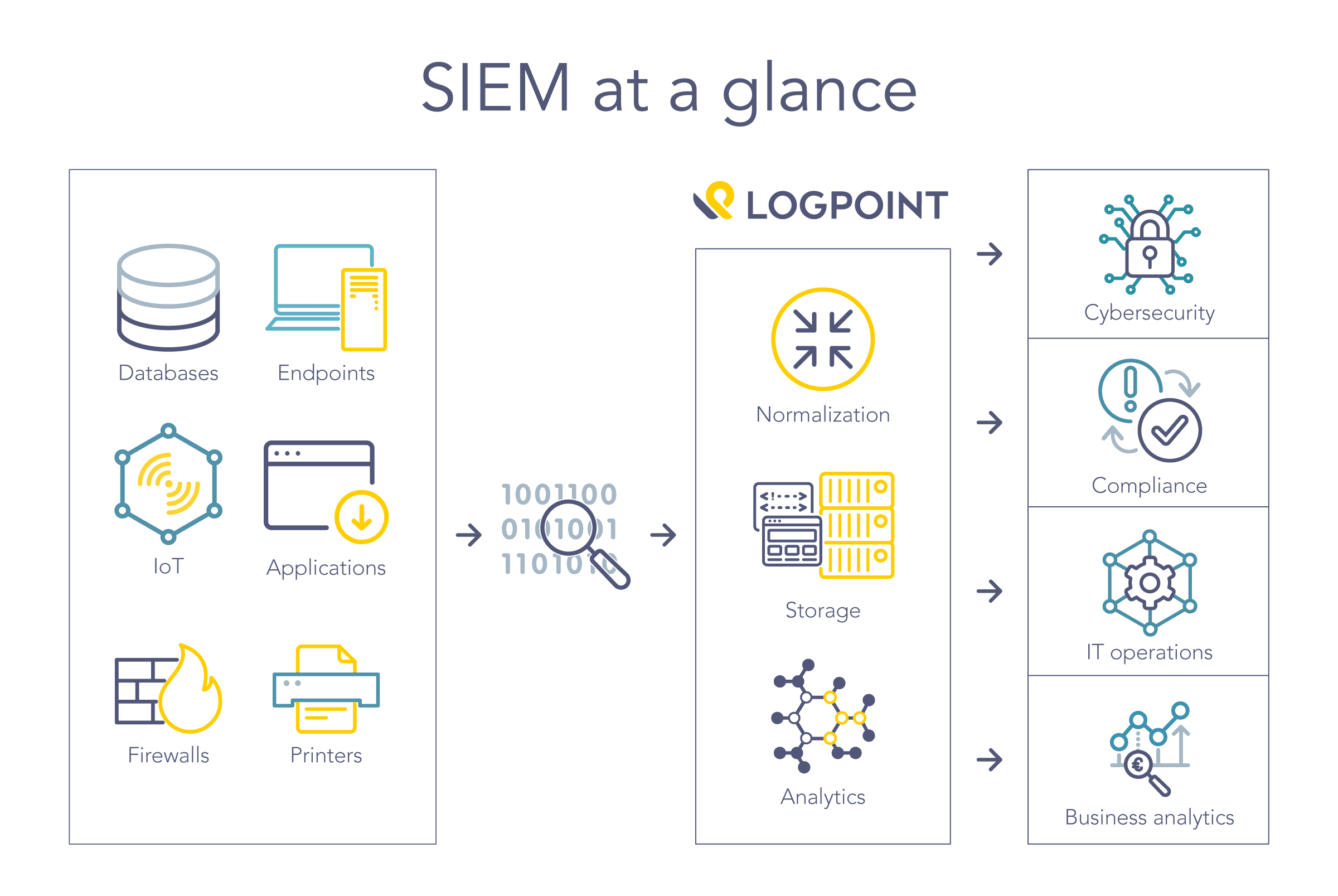
Read MoreWhat is SIEM Event Correlation?
(Security Information and Event Management) Gives Security teams Enhanced Threat Detection
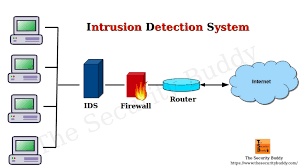
Read MoreWhat Is Intrusion Detection?
Intrusion Detection is the process of monitoring network traffic and system activity to identify and respond to potential security threats.
Read MoreWhat is a Vulnerability Assessment?
Its the process of identifying and potential security weaknesses in an organization’s systems, networks, and applications.
Read MoreWhat are Email Alerts?
Email alerts are notifications that are automatically sent to users when specific events occur providing timely information to users.
Read More